The WannaCry Ransomware Attack Explained
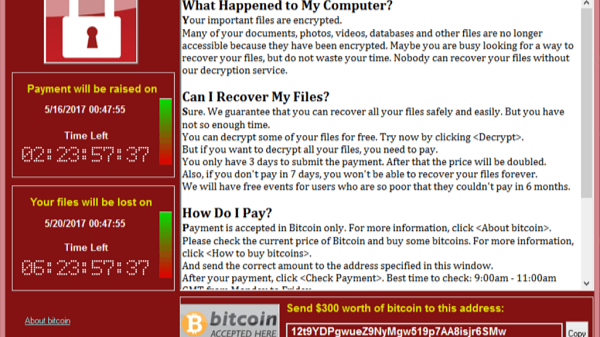
WannaCry was a crypto ransomware worm that affected an estimated 230,000 Microsoft Windows systems globally in 2017. A ransomware attack works by encrypting a system’s files and/or system and withholding access until the system owner pays a ransom, usually in the form of a cryptocurrency exchange, though there is no certainty that an attacker may release or decrypt the system files upon payment. A worm is a malicious software program that automatically spreads itself to multiple computers in a network by using operating system vulnerabilities to propagate across computers [2].
Within the NHS, the attack led to considerable disruption, affecting at least 34% of health trusts in England, facilitating the cancellation of thousands of appointments and operations and rendering medical equipment and devices unusable [1].
Network infection and propagation and execution
WannaCry entered the NHS network by exploiting the SMBv1 vulnerability [4] in Windows Operating Systems, nicknamed EternalBlue by the NSA. The EternalBlue exploit allowed specially-crafted data packets into vulnerable hosts on the network – such as devices on the NHS network – by sending a low-level network NT-Transaction request to a target. The request contained a malformed payload consisting of a sequence of No-Operation Instructions (NOPs) [8] to create a buffer overflow, facilitating more reliable execution of shellcode, and put the system into a state that could execute code with kernel-level privileges. Additional requests are sent where the request data portion holds the shellcode and encrypted payload that launches the malware on the remote machine through a service called mssecsvc.exe [8]. Wannacry’s exploit chain used a backdoor tool called DoublePulsar to install and execute itself [5].
Mssecsvc.exe also creates and launches tasksche.exe, which helps the malware persist, and in turn leads to the encryption of files and display of the malware interface [9].
Once WannaCry was installed on a device and the EternalBlue vulnerability had been triggered, WannaCry was able to scan the local network to find other vulnerable devices with exposed SMB ports (typically port 139 or 445). The running malware service then used the EternalBlue vulnerability again to gain access to the identified machines and deliver the malware payload.
Vulnerability analysis and lessons learned
A kill switch was activated by cybersecurity analyst and researcher Marcus Hutchins, who created a DNS sinkhole by registering the domain iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com [2] that WannaCry queried upon startup. It is theorised that this stopped the attack because WannaCry sent a query to this domain to ascertain whether it was being run in a sandbox or not. If it were, then the response from this domain would trigger WannaCry to not run, so as to remain undetected in sandbox environments. Registering the domain meant that the query would return a valid response each time that would trick the ransomware into thinking it was in a sandboxed environment.
Following the incident, better education over the integrity of personal systems and cyber attacks was highlighted. Two months before the attack began, Microsoft released the MS17-010 security patch [4] to mitigate against Eternalblue, however many individuals and organisations were still left vulnerable to the exploit because they did not regularly update their operating systems [3].
Whilst keeping software up to date would improve resilience to WannaCry and vulnerabilities in general, there are also a number of other ways this could have been achieved in this context, including:
- Blocking SMBv1 related ports: The network file sharing protocol Server Message Block (SMB) was the specific component within Windows OS that WannaCry exploited. One way to remediate this vulnerability would be to block SMB related ports (UDP 137, 138 and TCP 137, 139, 445) in the system firewall [6].
- Using vulnerability / malware scanners: Using anti-virus to detect system vulnerabilities early can suggest early action to avoid disruption.
- Preparing clear guidance and education for cyber attacks: In the case of the NHS, there was no established protocol or designated leadership in place for responding to the event, which resulted in confusion and uncertainty about the appropriate course of action for affected parties.
- Apply the principle of least-privilege to systems and services and run all software as a non-privileged user without administrative privileges [7].
- The SMB protocol facilitates file-sharing on local networks. Therefore it is best to disable this setting on your computer if it should not be in use.
Bibliography
[1] National Audit Office, ‘Investigation: WannaCry cyber attack and the NHS’, National Audit Office, Apr. 2018[Online]. Availablehttps://www.nao.org.uk/wp-content/uploads/2017/10/Investigation-WannaCry-cyber attack-and-the-NHS.pdf.
[2] CLOUDFLARE, (2017, ), What was the WannaCry ransomware attack?, Cloudflare.com. [Online]. Available: https://www.cloudflare.com/en-gb/learning/security/ransomware/wannacry-ransomware/.
[3] Kaspersky, (2024, ), What is WannaCry ransomware?, Kaspersky.com. [Online]. Available: https://www.kaspersky.com/resource-center/threats/ransomware-wannacry.
[4] C. Burdova, (2020, June.18), What Is EternalBlue and Why Is the MS17-010 Exploit Still Relevant?, Avast. [Online]. Available: https://www.avast.com/c-eternalblue.
[5] N. Latto, (2020, February.27), What is WannaCry?, What is WannaCry? [Online]. Available: https://www.avast.com/c-wannacry.
[6] NHS England, (2017, April.25), SMB EternalBlue and DoublePulsar Exploit, NHS Digital. [Online]. Available: https://digital.nhs.uk/cyber-alerts/2017/cc-1353.
[7] CIS Center for Internet Security, ‘EternalBlue Security Primer’, CIS Center for Internet Security. Jan. 2019[Online]. Availablehttps://www.cisecurity.org/wp-content/uploads/2019/01/security-primer-eternalblue. pdf.
[8] Mandiant, (2017, May.26), SMB Exploited: WannaCry Use of ‘EternalBlue’ | Mandiant, Google Cloud Blog. [Online]. Available: https://cloud.google.com/blog/topics/threat-intelligence/smb-exploited-wannacry-use-of-etern alblue/.
[9] A. Berry et al., (2017, May.23), WannaCry Malware Profile | Mandiant, Google Cloud Blog. [Online]. Available: https://cloud.google.com/blog/topics/threat-intelligence/wannacry-malware-profile.
